Malware Detection in Windows Using Deep Learning Classification Approach
Keywords:
Windows Malware, Malware Detection, Deep Learning, ClassificationAbstract
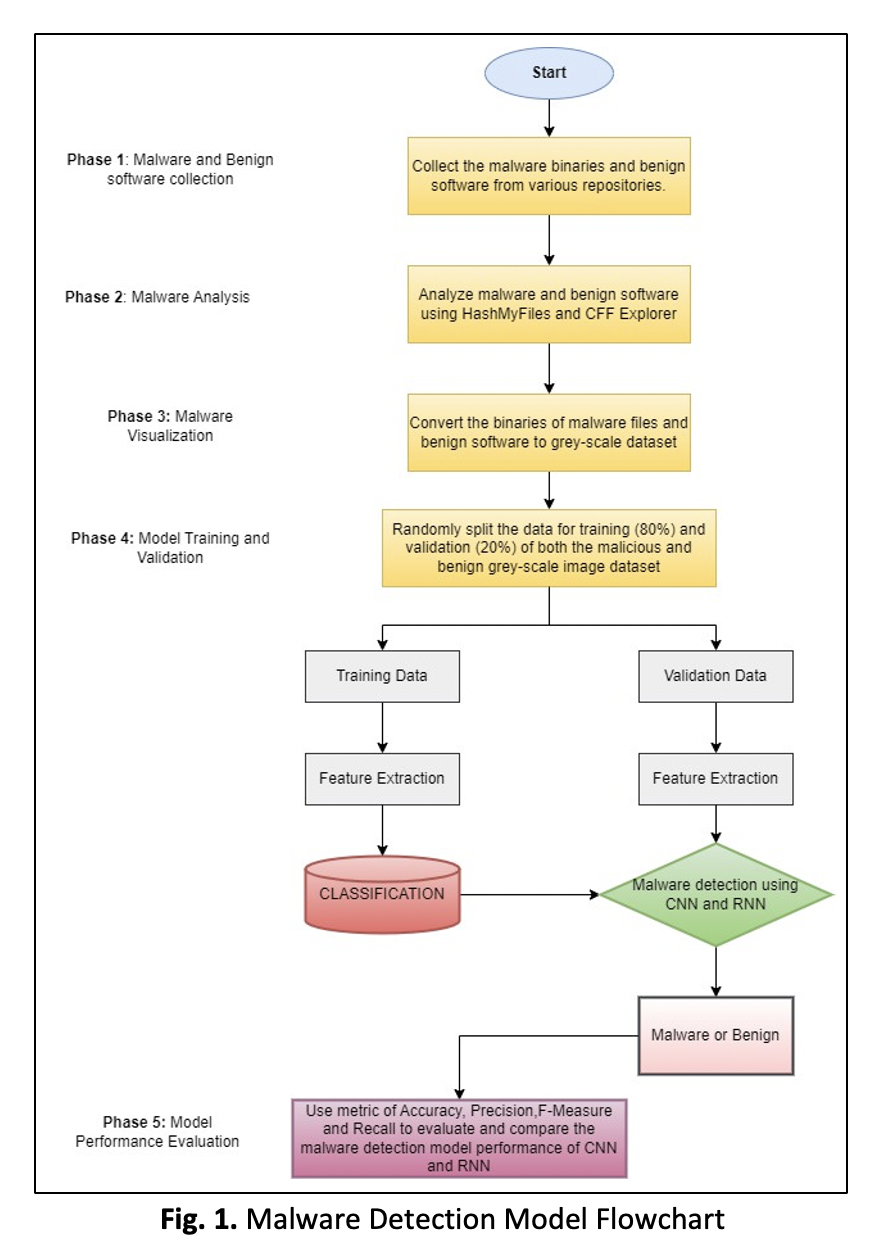
Microsoft Windows is the most common operating system, and because of its global popularity, it is also the most popular platform for hackers to target. It is also susceptible to security flaws. According to the Common Vulnerabilities and Exposures (CVE) database, which tracks known system vulnerabilities, Microsoft had over 660 dangerous security holes, 357 of which were associated with Windows 10. Thus, users may also be at risk because of security flaws in the Windows applications they employ or because of attacks on connected devices. Windows malware has been a major threat to computer software for decades, putting millions of people in danger. An attacker creates it to disrupt computer operations, gather sensitive information, or gain access to private computer systems. The increasing number of zero-day vulnerabilities and the rapid growth of Windows malware require efficient and accurate malware detection. Thus, this paper discusses Windows malware detection using a deep learning classification approach. In this study, the samples of Windows malware were analysed using malware analysis tools such as HashMyFiles and CFF Explorer. Subsequently, the malware visualisation was used to convert the binaries of malware files to generate a grayscale dataset. The classification process implemented using CNN and RNN for malware detection was being evaluated. Using the Metric Formula Definition Accuracy, the performance of Convolutional Neural Network (CNN) and Recurrent Neural Network (RNN) malware detection models in Windows has been tested. According to the models, CNN is doing better, providing an accuracy of 97.5 percent in detecting malware, whereas RNN provides an accuracy of 88.5 percent, respectively. This study evaluated the accuracy performance between the CNN and RNN architecture models.
Downloads