Advanced Persistent Threat Detection Based on Network Traffic Noise Pattern and Analysis
Keywords:
Advanced Persistent Threat, Zero Day Vulnerabilities, APT, Cyber AttackAbstract
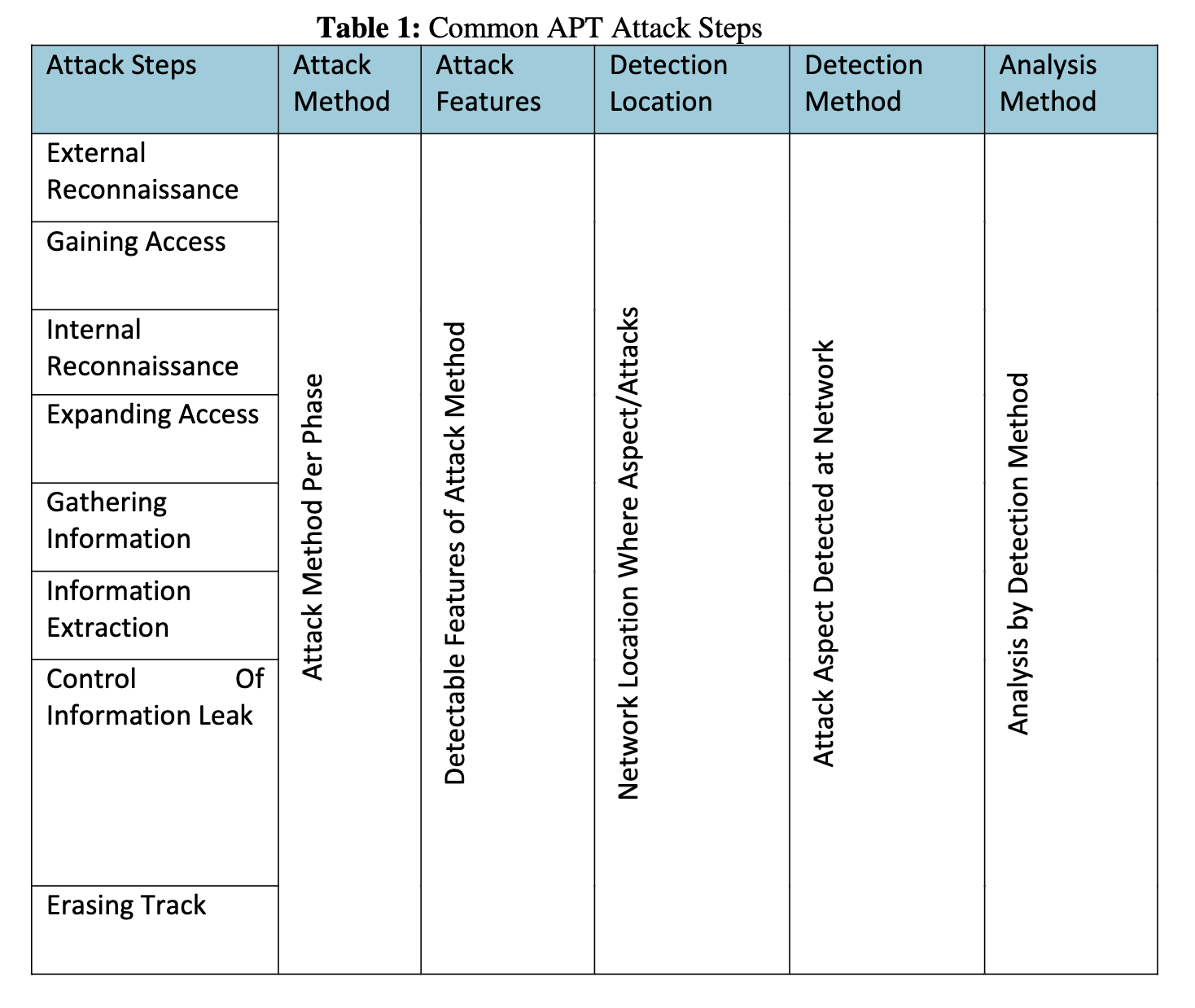
Advanced persistent threat (APT) is a network attack in which an unauthorized person gains access to a network and remain undetected for as long as they can. The intention of an APT attack is to steal data and eavesdropping rather than to cause damage to the network or organization. The problem of APT is the techniques used are stealth oriented and detection of APT attack has been difficult and even almost impossible in the early stage of penetration by exploiting Zero Day Vulnerabilities. This research is aimed at different angles of perspectives in order to detect APT attack by focusing at different areas besides Zero-Day Vulnerabilities. The new approach will detect APT by analyzing the traffic in between attacker and victim in a controlled virtual environment. By analyzing the traffic, this research has collected some samples of evidence in order to aid in APT detection. The achievements of this research are the evidences of connection and traffic patterns of each attack function recorded in traffic monitoring tools. All data were collected to be analyze and patterns of communication were recorded in a graph form in order to provide a clear picture for the researcher to identify the common pattern as an evidence to be picked up when an attack is going on and able to alert the victim. The future work of this research is to implement proposed framework with the actual network of computers with real life networking peripherals and real computer system instead of virtual environment. Besides, this research aimed to analyze the “Knock On” technique used by hacker to contact the C & C Server on demand
Downloads