Experimental Analysis of Trojan Horse and Worm Attacks in Windows Environment
Keywords:
Remote Access Trojan (RAT), vulnerability of operating system (OS), malware activity, worm attack, cyber threatAbstract
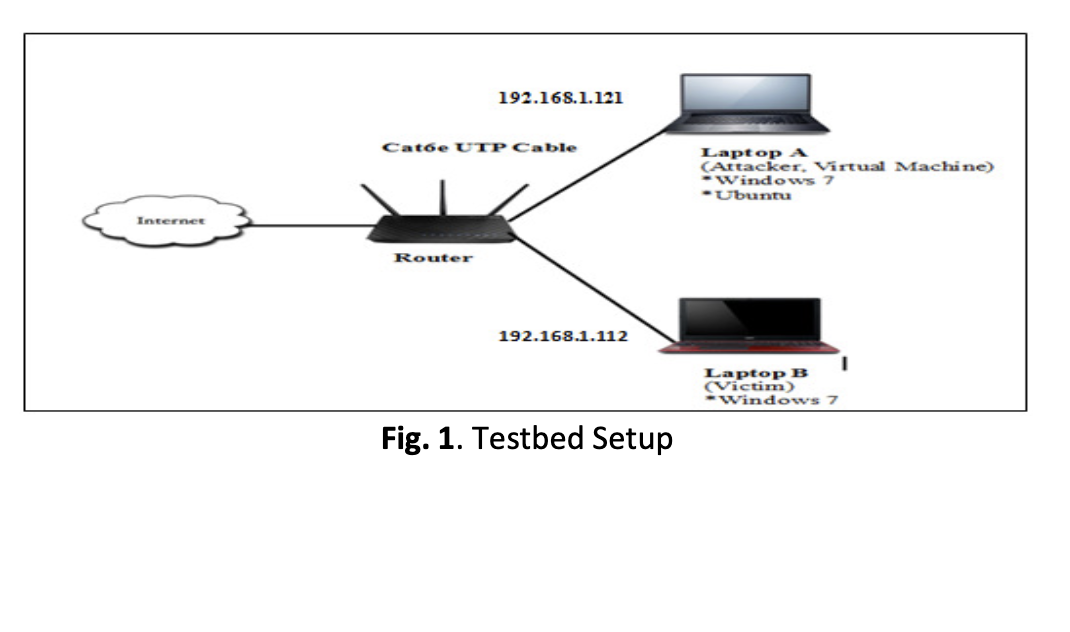
Trojan Horse is the most powerful malware that can produce an attack to penetrate into the network environment. Besides Trojan, another harmful malware known as Worm also can cause enormous damage to the computer system. Unfortunately, some users do not concern much on security because they thought there is not much valuable information can be obtained from them. The lack of awareness about computer and network security as well as misunderstanding of how malware attacks can occur, resulted in these users do not realize that their machines are at risk and they are exposed to several kind of potential cyber threats. Thus, this paper provides an insight on network vulnerability and presents some demonstrations of Remote Access Trojan (RAT) attack and worm file duplication attack via experimental tesbed. Then, Wireshark and some malware scanning tools such as Virus Total, MalwareBytes and Avast AntiVirus were also used for malware detection. The findings show that these attacks are possible and can be easily conducted to meet the purpose of the attackers. Therefore, educating the public to pay extra concern on malware vulnerabilities and to equip themselves with knowledge and skills to face the security challenges due to malware attacks is crucial.
Downloads